

Updated · Feb 11, 2024
Updated · Oct 25, 2023
Harsha Kiran is the founder and innovator of Techjury.net. He started it as a personal passion proje... | See full bio
Florence is a dedicated wordsmith on a mission to make technology-related topics easy-to-understand.... | See full bio
Large corporations are at risk for data breaches. Sensitive information collected by companies adds more value to the organization.
A data breach can be costly. In 2022, the cost of a data breach reached an average of $4.35 million.
Data Loss Protection (DLP) is a cybersecurity solution that helps organizations keep these sensitive data within their parameter. It exposes and halts data leakage through different practices and protocols, heightening data security.
In this article, learn about Data Loss Prevention (DLP) and how it can be an excellent investment for business strategy.
|
🔑 Key Takeaways:
|
Data Loss Prevention, or DLP, is a section of a company’s comprehensive security strategy. Aside from detecting and preventing data loss, it also focuses on the mishandling of data, exfiltration, and unwanted deletion of sensitive data.
Data loss refers to losing essential files after a cyberattack. DLP refers to the practices and protocols that prevent sensitive data from being transferred outside organizational parameters.

Implementing DLP allows businesses to identify, monitor, and spontaneously halt the exposure of confidential information.
Companies must first identify and build a policy around the data that needs protection to deploy DLP in their systems. After this, organizations take a proactive approach to monitoring user activity.
Data protection measures are deployed for data actively in transit from one location to another, currently accessed, and not moving data. Although data at rest are less vulnerable than those in motion, they are considered more profitable targets.

Once security measures are in place, organizations must concurrently detect and respond to threats. Sending alerts and encrypting the data can be done. Specific formulas include regular expression patterns, security information and event management (SIEM), and intrusion prevention systems (IPS).
This way, businesses can systematically detect suspicious movements and automatically alert the IT department. Plus, there are many types of data threats that IT teams must prepare for.
Hackers can deploy simple hacking methods to steal data from an organization. Here are some common methods they use:

Extrusion
This method is about stealing confidential data. It uses techniques like phishing and different types of malware attacks to penetrate the restricted perimeters of target companies. Common exfiltrated data includes log-in credentials and intellectual property.
This type of data threat happens when a current or former employee uses his access to move sensitive data outside the organization. Aside from employees, clients and anyone with a transaction with the company can also become insider threats.
Unintentional data exposure is also considered a type of data threat. Accidentally sending out sensitive information outside the organization by an employee or non-employee poses a danger to the company.
Protecting against these common types of data threats is crucial for any organization to safeguard sensitive information and maintain the security of its operations.
|
✅ Pro tip! Protect your data by using strong, unique passwords with a password manager, enabling two-factor authentication, staying updated on software patches, and being cautious about email links and attachments to avoid common threats. |
The best prevention for data leakage is a combination of technology, system controls, employee awareness, and education.
A holistic and comprehensive approach can save businesses billions in losses. The following are the different procedures you can consider:
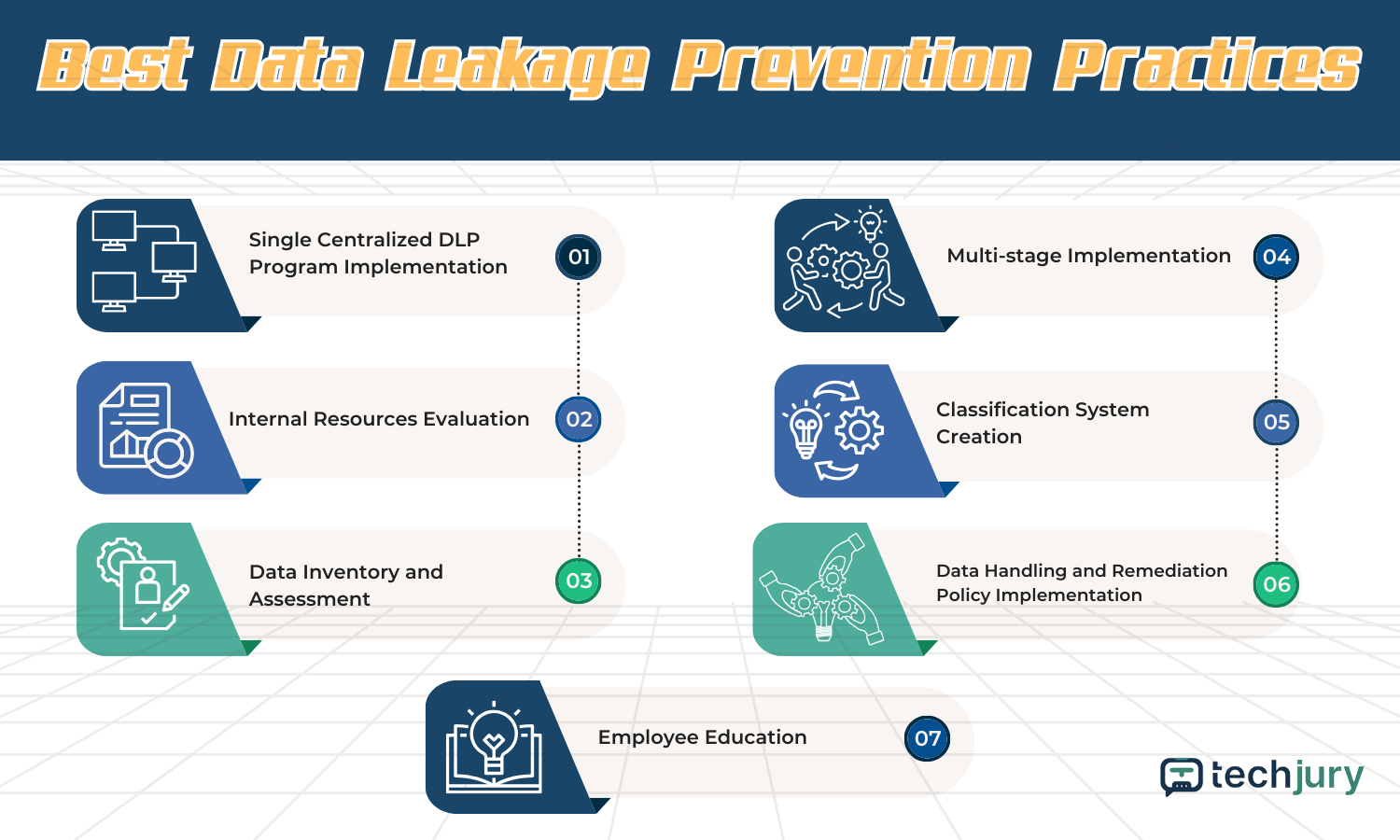
It is beneficial for companies to use a solid and centralized DLP program instead of inconsistent ad hoc security programs. An incoherent system used by different departments and units can lead to weak data protection. It can result in a lack of data visibility on departments not supported by DLP programs.
DLP experts are also a significant factor in the creation and execution of DLP programs. Organizations must have well-versed personnel in DLP risk analysis, data breach response, data protection regulation, and DLP awareness training. DLP experts can be internal employees or third-party consultants. They will act as data protection officers (DPOs) under GDPR.
Data inventory is an organization's first step in a DLP program. Companies must be able to locate all relevant data and then assess the value of each. An organization must identify the information assets and categorize them accordingly. After this, IT teams must determine the risk integrated with each data.
Companies need to deploy DLP programs in multiple stages. DLP is known as a long-term process, so it makes prioritization important. It is best to implement the DLP software components in areas that need urgent protection rather than deploying it all at once.
Creating a taxonomy or classification guide for every data type helps build DLP policies. The structured and unstructured data classification framework can help the workforce identify which data are confidential, regulated, personally identifiable information (PII), intellectual property, etc.
After creating the classification system, create or update the DLP policies focusing on handling all data types, especially sensitive data. With this, organizations can use pre-configured rules based on government policies like GDPR. Then, the DPO can tweak policies to cater to the organization's needs.
Employees must be well-informed about security policies. Companies should implement DLP awareness training to ensure employees' compliance and acceptance of DLP procedures. Training can include classes, online training, regular emails, and written reports to enhance employees' understanding.
A well-structured DLP program addresses data protection challenges. Equally important is educating employees about security policies to ensure their understanding and compliance. This pragmatic approach enhances overall data security and minimizes risks for organizations.
|
✅ Pro tip! Prioritize data classification by defining what needs protection and then applying strict access controls to minimize data leakage risks. |
DLP is the game-changer for business firms in the digital space. It creates the protection they need to continue their business. Although cyberattacks will always be present, procedures like DLP can significantly save companies in times of cyber crisis.
If you are a business owner, consider assessing your company’s DLP. See if it is updated or if it is time to upgrade your systems.
Network DLP, endpoint DLP, and cloud DLP are the three types of DLP.
The three primary goals of DLP are to address the pain points of many organizations: personal information protection and compliance, intellectual property (IP) protection, and data visibility.
The four elements of a full-suite DLP tool are a central management server, network monitoring, DLP storage, and endpoint DLP.
Your email address will not be published.
Updated · Feb 11, 2024
Updated · Feb 11, 2024
Updated · Feb 08, 2024
Updated · Feb 05, 2024



