

Updated · Feb 11, 2024
Updated · Nov 17, 2023
Raj Vardhman is a tech expert and the Chief Tech Strategist at TechJury.net, where he leads the rese... | See full bio
April is a proficient content writer with a knack for research and communication. With a keen eye fo... | See full bio
Cybercriminals continuously seek new ways to exploit companies and individuals by targeting the vulnerabilities in their devices and networks.
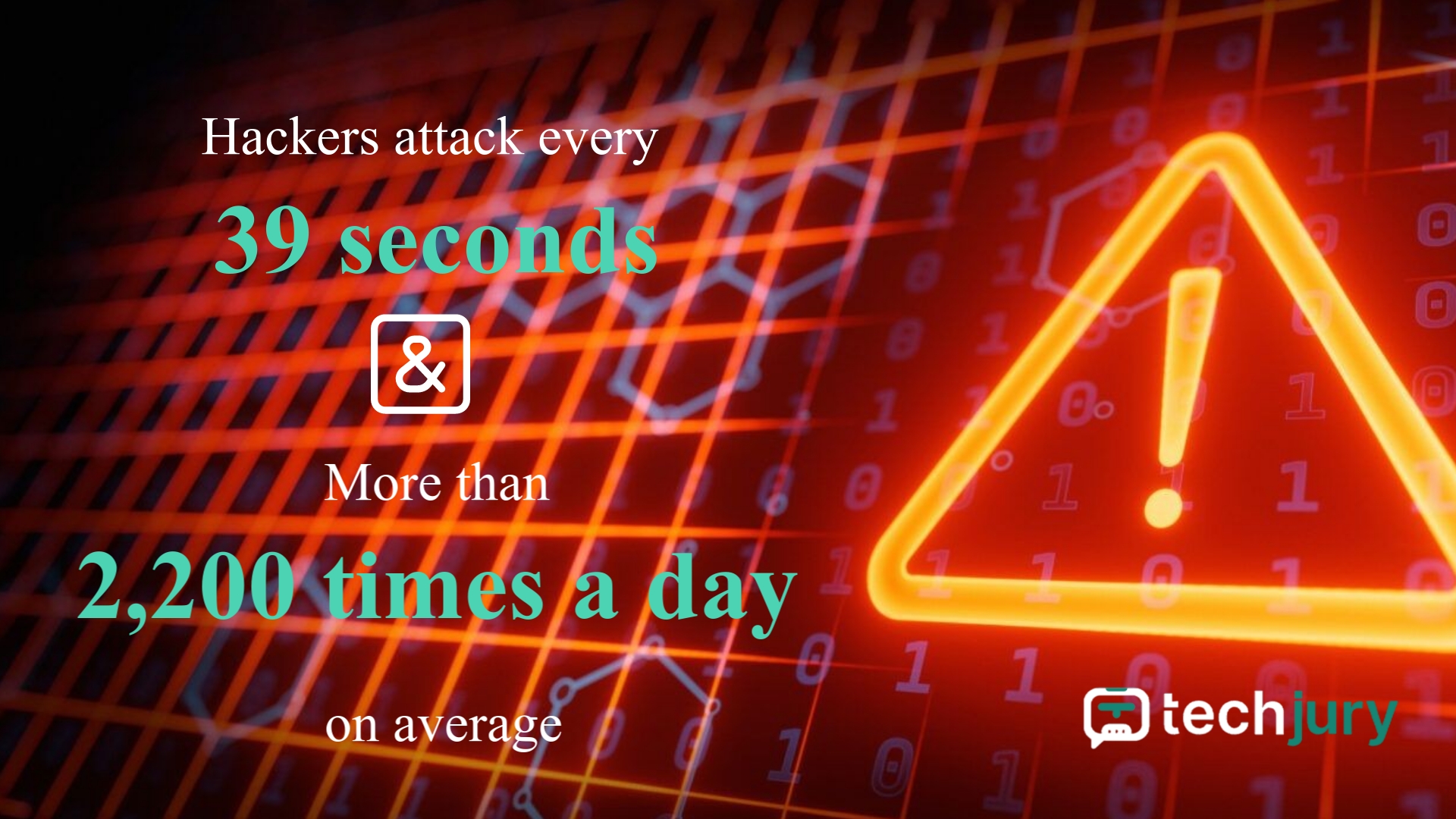
One study says that there are more than 2,200 cyber attacks every day. Making that one attack every 39 seconds.
Among hackers' various malicious tactics, one stands out—downgrade attacks.
These attacks are known for potentially compromising the security of your valuable data and online activities.
This article will unravel the intricacies of these attacks, explore their diverse forms, and, most importantly, arm you with effective strategies to prevent their assault on your devices.
|
🔑 Key Takeaways
|
A downgrade attack is a form of cyber attack where a hacker forces a system or network to revert to an older, less secure version of software or communication protocols.
The aim? To take advantage of known weaknesses and loopholes patched up in newer versions and, as a result, bypass advanced security measures.
When someone updates their software to the latest version, the attacker strikes by cleverly manipulating the communication between a client and a server. Tricking both ends into using an outdated, compromised version.
|
🎉 Fun Fact: Downgrade attacks use "old tricks" to exploit modern security measures, tricking systems into using less secure versions and gaining unauthorized access to data. It's like using an ancient key to unlock a digital fortress! |
The following sections will explore the mechanisms behind downgrade attacks and the different types they come in.
Downgrade attacks operate by taking advantage of one simple fact: older versions of software and communication protocols tend to have more vulnerabilities than their updated counterparts.
This weakness becomes a golden opportunity for the attacker to breach a system’s security defenses.
A common way to carry this out is through a man-in-the-middle (MITM) attack, where the attacker interferes and manipulates communication between the user and server.

The server will be forced to use older and less secure protocols of TLS (transport layer security) or SSL (secure socket layer).
This attack often tricks visitors to a website into using an unsecured HTTP connection instead of the secure HTTPS in web applications.

Protocols like STARTTLS are vulnerable to downgrade attacks because they fall back to unencrypted communication when encryption is impossible.
Understanding these mechanics is crucial to staying one step ahead and protecting yourself from falling prey to different downgrade attacks.
|
Good to know! Downgrade attacks can target not only software and protocols but also device firmware. Firmware is the low-level software embedded in hardware components. Attackers can downgrade the firmware and potentially compromise the entire network. |
Downgrade attacks come in various forms, each targeting different aspects of our devices and networks.
Here are some of the most notorious types:
Poodle is a downgrade attack that targets SSL 3.0, an older version of the SSL protocol. The attacker forces communications to fall back to less secure versions and gains access to sensitive information.
This attack takes advantage of a weakness in SSL/TLS protocols, and the attacker forces weaker export-grade encryption. This paves the way for them to crack the encryption and eavesdrop on the communication.
The Logjam attack targets the Diffie-Hellman key exchange protocol. Like the FREAK attack, the attacker downgrades the connection to a lower level of encryption. From there, they exploit weaknesses in the algorithm and decrypt any intercepted communication.
This attack focuses on SSL/TLS protocols, particularly those using block cipher algorithms like AES-CBC. This allows them to decrypt secure cookies and gain unauthorized entry.
The attacker takes advantage of vulnerabilities in securing data through digital signing and hashing procedures. Hashing is like converting information into a unique code while signing verifies the authenticity of data.
By exploiting these weaknesses, attackers can undermine communication security, making intercepting and deciphering sensitive data easier.
|
In a nutshell: Downgrade attacks come in different forms and target various aspects of devices and networks. Notable types include POODLE, which targets the protocol SSL 3.0 to compromise sensitive information. FREAK, Logjam, BEAST, and SLOTH are other types that exploit weak encryption, downgrade connections, and undermine communication security. |
After understanding the types of downgrade attacks, it’s crucial to learn preventative measures to safeguard our devices and networks.

Here are some effective strategies to protect yourself from downgrade attacks:
1. Keep Software and Firmware Up-to-Date
Regularly update your software, applications, and operating systems to ensure you have the latest Enhancements and security patches. Most importantly, update to the latest TLS version. This reduces the risk of being a victim of vulnerabilities and exploitation.
2. Enable Automatic Updates
Whenever possible, enable automatic updates for your devices. This ensures you receive the latest security updates without delay, reducing the window of opportunity for hackers to exploit downgrade vulnerabilities.
3. Exercise Caution with Application Downloads
Download applications from reputable sources such as official app stores or trusted websites. Be vigilant when prompted to install or use older versions of applications, as they may contain known security flaws.
4. Implement Robust Network Security Measures
Utilize firewalls, intrusion detection systems, and strong encryption protocols to protect your network from unauthorized access and interception.
5. Practice Phishing Awareness
Be cautious of suspicious emails, messages, or calls that attempt to persuade you to install or use older software versions. Exercise skepticism and verify the authenticity of such requests before taking any action.
|
Pro tip! Keep your software and firmware up-to-date, enable automatic updates, exercise caution with application downloads, implement robust network security measures, and practice phishing awareness to protect your device from downgrade attacks. |
By following these tips and staying informed about the latest security practices. You can significantly reduce the risk of falling victim to downgrade attacks and protect your devices and networks from malicious actors.
To conclude, safeguarding our devices and networks from downgrade attacks and any other cybercrime that have been increasingly becoming prevalent in today’s digital age.
We can take more proactive steps by understanding how these attacks work and how to protect ourselves.
Remember to stay informed, remain vigilant, and prioritize cybersecurity in this world full of digital threats. Stay secure by implementing good internet security habits and prioritizing your digital safety.
Yes, mobile devices are vulnerable to downgrade attacks, especially if they run outdated software or use older versions of communication protocols.
No, while downgrade attacks can be executed remotely, others may require physical access to the device or network.
Various security solutions and antivirus software incorporate features that can help prevent downgrade attacks. Research and choose reputable products that align with your security needs.
Your email address will not be published.
Updated · Feb 11, 2024
Updated · Feb 11, 2024
Updated · Feb 08, 2024
Updated · Feb 05, 2024



