

Updated · Feb 11, 2024
Updated · Nov 16, 2023
Antanas Rimeikis is a dynamic Cybersecurity copywriter at surfshark.com. Known for his creativity, g... | See full bio
Florence is a dedicated wordsmith on a mission to make technology-related topics easy-to-understand.... | See full bio
Around 30,000 websites are hacked daily. This is why cybersecurity tools like antivirus software and VPNs are on the rise.
However, not all users are familiar with their devices’ innate defense against online threats like malware and viruses. This first line of protection is called “firewall.”
Similar to how countries have borders and border patrol, each device has a firewall. The main role of established borders and firewalls is to prevent any threats from entering.
In this article, you will learn more about the border patrol of computers—firewalls. Continue reading to understand what it is, how it works, and more.
|
📖 Definition A firewall is a security system or network security device sitting between an internal private network and an external public one. The term “firewall” comes from the idea of physical walls preventing the spread of fire in emergencies. |
Firewalls act as protective membranes that check and filter incoming and outgoing traffic. Its job is to allow or deny entry or exit of any data coming its way.
Since all data on the web is transported as data packets, all firewalls can be considered to be packet-filtering.
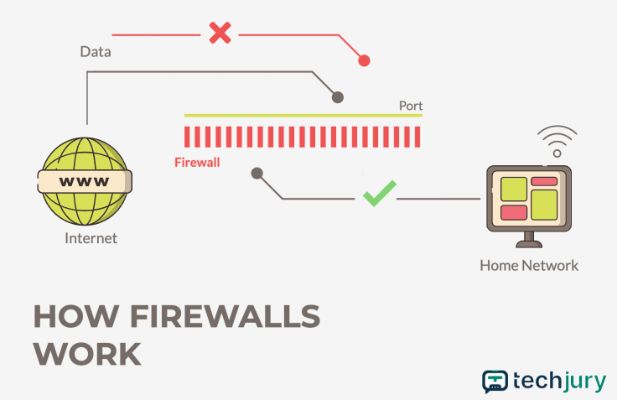
Once data reaches a device (or a network), it enters it via the entry point—called a port. It is at that port that data gets inspected by a firewall.
The same process happens with data that leaves the device or a network—it gets inspected at the exit point. In simpler terms, firewalls overlook and manage network communication.
To truly understand how firewalls work, taking a deep dive into the Open Systems Interconnection (OSI) model is necessary.
You will learn just that in the next section. Keep reading.
The OSI model helps people determine the required hardware and software to build their network, including firewalls. The model consists of seven layers.
These layers are:
Different firewalls operate on distinct levels of the OSI model. Check out how data travels through these layers using Bytebytego’s illustration below:
|
How does a firewall know what data to let in or out? It does so based on predetermined security rules. All of which depends on the type of firewall.
There are two major categories of firewalls. The first one is hardware-based, which is like a special computer you put on a network to protect it.
While the second category is software-based, where special software on your device helps manage your network. These are usually called Software-as-a-Service (SaaS) firewalls.
Out of these two categories emerge a multitude of firewall types, such as:

Learn more about each firewall type below.
A NAT firewall protects a network from unauthorized access and conceals the private IP (Internet Protocol) addresses of devices within the network.
NAT also allows multiple devices in a private network to share a single public IP address when communicating with devices outside the network.
This type of firewall also operates on the network layer. It is usually found on routers and allows internet traffic to pass through only if a device on the private network requests it.
Referred to as the "traditional," a stateful inspection firewall monitors all activity from opening a connection until it is closed.
It inspects the data packet and permits or denies movement based on the packet's state, port, and protocol. This firewall normally works on network and transport layers.
The packet examination is determined by administrator-defined rules and the context of the communication—such as using information from previous connections and packets from the same connection
|
🎉 Fun Fact: The stateful firewall was invented by Gil Shwed in 1993. He is the founder and CEO of Check Point Software Technologies Ltd, one of today’s leading cybersecurity solution providers. |
A stateless firewall allows or denies packets into its network based on the source and the destination address.
This firewall watches the network traffic. However, it does not inspect it or its state, ergo stateless.
An example of this firewall is the file transfer protocol (FTP), which is the most common way of receiving the sending files between two computers.
This type is also known as application-level gateways or ALGs. It is a gateway from one network to another for a specific application.
A proxy firewall serves as an intermediary for clients and servers (proxy). It can conduct stateful and deep packet inspection (DPI) to weed out malicious traffic.
Proxy firewalls operate at the application layer. That means they can understand particular application protocols like HTTP, FTP, TCP, ACL, and more.
|
✅ Pro tip: If you plan on getting a proxy firewall, consider acquiring one that supports SSL/TLS inspection for stronger security. This feature allows the firewall to decrypt and inspect encrypted data, protecting devices against threats hidden in encrypted content. |
As the name implies, packet filtering happens across multiple levels: network, transport, and application layers.
When filtering, it also compares the filtered packets against known and trusted ones. Trust can only be determined by the packet’s communication state.
To “pass the trust test,” a data packet must go through each inspection layer separately. Hence, the multilayer inspection bit.
A next-generation firewall combines regular stateful inspection technology with additional security features to combat modern threats.
NGFWs are an industry standard for enterprise use. The specifics differ from one company to another.
Sometimes, NGFWs are interchangeably called Unified Threat Management (UTM) firewalls.
|
A UTM is the child of three (sometimes more) cybersecurity measures. These can be:
|
A virtual or cloud-based (or cloud-native) firewall does the same thing as its hardware-based counterparts.
However, the difference lies in the deployment and management, which is done from the cloud.
It provides security for cloud-based applications, virtualized environments, and distributed networks.
This firewall is a great solution in circumstances when and where hardware firewalls are nearly impossible to install—like public and private cloud environments, software-defined wide area networks (SD-WANs), and software-defined networks (SDNs).
Besides, cloud-based firewalls offer scalability, flexibility, and centralized management across multiple locations.
|
✏️ Note: To know more about firewalls and other ways to protect your devices, subscribe to Surfshark’s bi-weekly newsletter for tips, updates, and more. |
A firewall is a security device that barricades unauthorized access to a network. It inspects, monitors, blocks, and redirects data traffic.
Also, it controls access to any sites and apps. A firewall does all of this and more while defending you and your devices from malware threats.
You can get anti-virus software, VPNs, and other cybersecurity tools. However, it is still best to keep your firewalls up to protect your devices.
You need a firewall on your device to stay safe and protected from malware when browsing the internet. It’s best never to turn off your firewall. Keeping it up makes it near impossible to inject your network with malicious traffic.
Yes. If a firewall is outdated or guarding an app with vulnerabilities, a hacker can exploit a firewall—no matter its intricacy. Outdated firewalls and services with known issues are a security risk.
It’s best to have an antivirus AND firewall running at once. A firewall is usually enough. However, once a virus enters a device, there’s not much a firewall can do. An antivirus is great at keeping your device clean of malicious apps.
Your email address will not be published.
Updated · Feb 11, 2024
Updated · Feb 11, 2024
Updated · Feb 08, 2024
Updated · Feb 05, 2024



