

Updated · Feb 11, 2024
Updated · Nov 16, 2023
With a master's degree in telecommunications and over 15 years of working experience in telecommunic... | See full bio
Lorie is an English Language and Literature graduate passionate about writing, research, and learnin... | See full bio
Are you experiencing suspicious activities on your computer? Your device might be infected with the infamous Trojan Horse malware.
According to statistics, 58% of computer malware comes from Trojans. It is one of the most harmful types of malware. It can steal your information, spy on you, and damage your device without knowing it is already on your PC.
Find out more about this malware and how to protect yourself against it.
|
🔑 Key Takeaways
|
In technology, Trojan Horse is a type of malware that pretends to be legitimate software or code. It can also disguise itself as authentic files attached to emails.
This malware works when a user downloads the executable file (.exe). Once it’s installed, it will begin to attack the device.

Trojans often go unnoticed because the computer continues to work normally. It can visit websites and even banking applications without your consent.
|
📜 Etymology The term “Trojan” came from the Greek epic poem “The Aeneid.” In this story, Odysseus is a Greek warrior planning to attack the city of Troy. He made a giant wooden horse that would serve as a gift to Trojans to show they had surrendered. Trojans believed this trick. They celebrated upon receiving the gift, not knowing that Odysseus hid his men inside the horse. Once the Trojans were all drunk, the Greeks attacked the city. The Greeks used the Trojan Horse to trick and defeat the Trojans—similar to how the malware tricks a user by pretending it is real software. |
People refer to Trojans as "Trojan Virus." However, Trojan Horse is not a virus but a malware.
The distinction between viruses and Trojans is one of the common misconceptions in the digital world. Although they both can damage your computer, they are different.
Check the table below for their differences:
|
Computer Virus |
Trojan Horse |
|
Viruses attach to other files or programs and write their codes. You can still get a virus even if you downloaded a legitimate file. |
Trojans pretend to be legitimate programs. You can get Trojans because you downloaded what you thought was legit software or file. |
|
Viruses grow from one program to another, leaving infections that damage the system. |
Trojans access and extract users' sensitive information and system illegally. |
|
They cannot infect you unless you click, open, or run malicious programs. |
Trojans can not infect your computer unless you downloaded it. |
Besides its sneaky method of tricking users into installing, Trojan Horse malware became popular globally because of its severe effects—be it on a single device or a massive institution.
Here are some of the worst attacks caused by Trojan Horse malware:

The Emotet malware was first detected in 2014 when it targeted health and bank institutions. It became popular in 2018 when it infected Fürstenfeldbruck Hospital in Germany. It shut down 450 computers at that time.
This malware continued to spread because it used Outlook harvesting. It invaded victims' devices and sent phishing emails to contact lists. The emails contain Word documents that seem to be from a trusted source.
The US Department of Homeland Security considered this one of the most destructive cyberattacks in history.

In 2007, the world discovered Zeus or Zbot. Many people knew it after they attacked the Department of Transportation in the United States.
Zbot created a botnet that contains infected machines. The botnet targeted 74,000 FTP accounts in 2009. That same year, it also attacked 3.6 million computers in the US.
Included in these attacks are private entities, government offices, and banks. These are the following institutions that were infected:

From the name itself, this Trojan malware is because of European storms.
In 2007, Europeans received malicious emails containing weather bulletin updates. The severe weather they experienced made them believe that these were real.
This malware entered about 1 million computers in Europe and America. It delivered spam emails, stole information, and launched Distributed Denial-of-Service (DDoS) attacks.
Technology keeps on evolving, and so do online threats like Trojans.
In 1975, the first Trojan malware (ANIMAL) was created. From there, Trojans evolved into different variants. As of today, there are many Trojan types with complex forms.
Below are the types of Trojans that you should be aware of:
 Backdoor Trojans
Backdoor Trojans
This type of Trojan can make a “backdoor” on your device. It can access and control your computer by deploying malware into the Command and Control Center to monitor and steal sensitive information.
Downloader Trojans
This malware downloads and installs files on your laptop. It also puts malicious programs in your device without you knowing. Its primary purpose is to steal, disrupt, and damage your computer and devices.
Rootkit Trojans
The Rootkit is a Trojan Horse malware which is a collection of software. It acquires access both at the root or administrative level for machines.
It will also set up a backdoor exploit to deliver more malware if they are on your laptop. This type is challenging to detect and remove.
DDoS Attack Trojans
This type of Trojan is also known as Botnet, which are internet-connected devices infected with malware.
Botnets are usually invisible and do not have immediate effects on devices. Sometimes they control the device, but they typically attack silently.
In 2022, Microsoft reported 1,955 DDoS attacks daily—a 40% increase compared to the year before.
Once you get a Trojan Horse infection, it can spread to other computers and devices. However, you can remove this malware using the same techniques to remove viruses.
Try these simple and easy methods:
If you accidentally downloaded or installed a suspicious program, delete it immediately. Software with unknown origin can be a source of Trojan malware.
Here’s how you can delete any potentially malicious software:
|
Step 1: On your computer’s “Search Bar,” look for the “Application Manager.”
Step 2: Find any suspicious software or program. Step 3: Right-click and select “Delete” or “Uninstall.” Step 4: Go to your “Recycle Bin” and delete it permanently.  |
Nearly 89% of desktop users use antivirus software nowadays. It is an effective tool for your computer to prevent and fight malware.
If you still do not have antivirus on your device, you can get it this way:
Step 1: Search for the antivirus software that suits your needs.
Step 2: Install the software.
|
🔓 Security Note Always check if the software you’re installing is legitimate. Fake antivirus exists and can infect your device with more malware. |
Step 3: Once the program is installed, set it up and run a scan.
Step 4: Remove any detected malware or threat.
|
✅ Pro Tip If you’re confused about what antivirus software to get, you can start with Surfshark Antivirus. It offers scheduled scanning and real-time protection to keep your device safe 24/7. |
Sometimes, the methods mentioned above do not work. If that’s the case, your last resort is to reset your device.
|
⚠️ Warning This method deletes all your files permanently. Before you do this, make sure to back up all your necessary data. |
You can initiate the factory reset by following these steps:
Step 1: Go to your “Settings.”
Step 2: Click “Update and Security” and find “Recovery.”

Step 3: Look for “Reset this PC.”
Step 4: Click Get Started or Remove Everything.
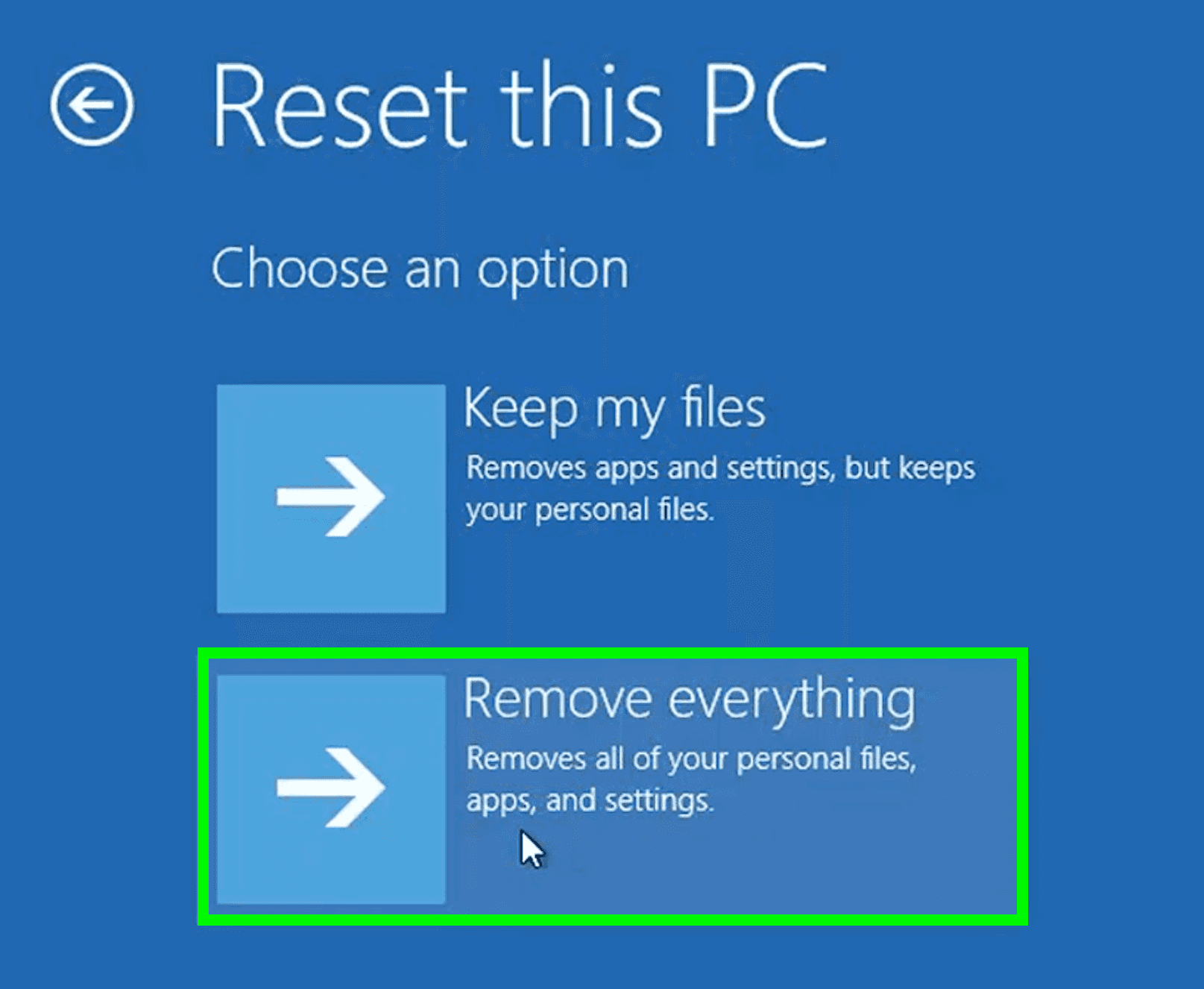
Step 5: Restart your laptop.
Cybersecurity measures should be implemented to avoid getting Trojans on your devices. Here are the safety precautions that you can take:
1. Install software from trusted sources only
Trojan Horse malware is good at making websites and software look as if they are legitimate. Always do thorough research before clicking any Download or Install buttons.
2. Never run a program or open attachments from unknown emails
Trojans can also be in emails. Once you receive suspicious emails with attachments, do NOT click or open them. The attachments may contain malware that can infect your device.
3. Do regular check-ups on your device
Even if your computer works normally, it is still best to have a routine check-up. Trojans can access your data without you knowing, so regular check-ups will help catch any chances of infection sooner.
4. Install an antivirus and use it regularly
Antivirus is a good tool to prevent and remove viruses and malware on devices. It can eliminate any threat to your device’s security.
Trojan Horse malware made it known to the world just how dangerous it can get. It can spy on you, damage devices, and more. Worse things can happen if you do not remove this malware immediately.
Always monitor your computer. If you notice something weird about your device, check what is going on. If your computer still has unusual activities after troubleshooting, seek professional help.
Yes. Trojan Horse malware does not only infect computers but mobile phones too. Slow performance and excessive data usage are common signs that your phone may be infected.
Unfortunately, no. Windows Defender cannot delete Trojans from the device. There are additional steps that you must take to remove this malware.
Yes, one of the everyday things malware can do is corrupt your files.
Your email address will not be published.
Updated · Feb 11, 2024
Updated · Feb 11, 2024
Updated · Feb 08, 2024
Updated · Feb 05, 2024



