

Updated · Feb 11, 2024
Updated · Nov 17, 2023
Driven by his experience as a hosting support staff for two years in Sofia, Nick tested and evaluate... | See full bio
Girlie is an accomplished writer with an interest in technology and literature. With years of experi... | See full bio
Living and working environments have innovative products that perform autonomous computations and connections. When these electronic devices can connect to other devices or networks, they’re called endpoints.
Endpoint devices are physical devices connected to a network or internet. They are an endpoint or access point on a distributed network.
In this article, you’ll learn about endpoint devices, how they work, and the level of cybersecurity they require.
 Any device used to connect to the internet is an endpoint device.
Any device used to connect to the internet is an endpoint device.
Simply put, when two people are interacting during a phone call, a connection is made between them. The endpoints of that connection are their phones.
Endpoint devices are also hooked up to a TCP/IP network. They’d have conversations with each other, passing information back and forth–– endpoint to endpoint.
Because of their nature, endpoint devices could be entry points for malicious actors. If a gap in the security system occurs, black hat hackers could use that vulnerability to enter a network.
Cybersecurity lapses in endpoint devices, such as no proper monitoring, could threaten your network security. The possible cyberattacks that could arise include phishing, different kinds of malware, and data breaches.
The different kinds of endpoint devices are:
Research center Ponemon Institute’s survey found that endpoint attacks were some of the most prevalent cybercrimes in 2020.
Moreover, among all endpoint devices, laptops are considered to be the most vulnerable. The same study discovered that 55% of professionals consider laptops most prone to cyberattacks.
81% of businesses experienced endpoint attacks caused by some form of malware, and 28% involved compromised or stolen devices.
These figures highlight the massive security concerns that come with endpoint devices.

Hackers target endpoint devices instead of attacking your network directly because they’re a more accessible entryway. In other words, they’re like doors to valuable digital assets.
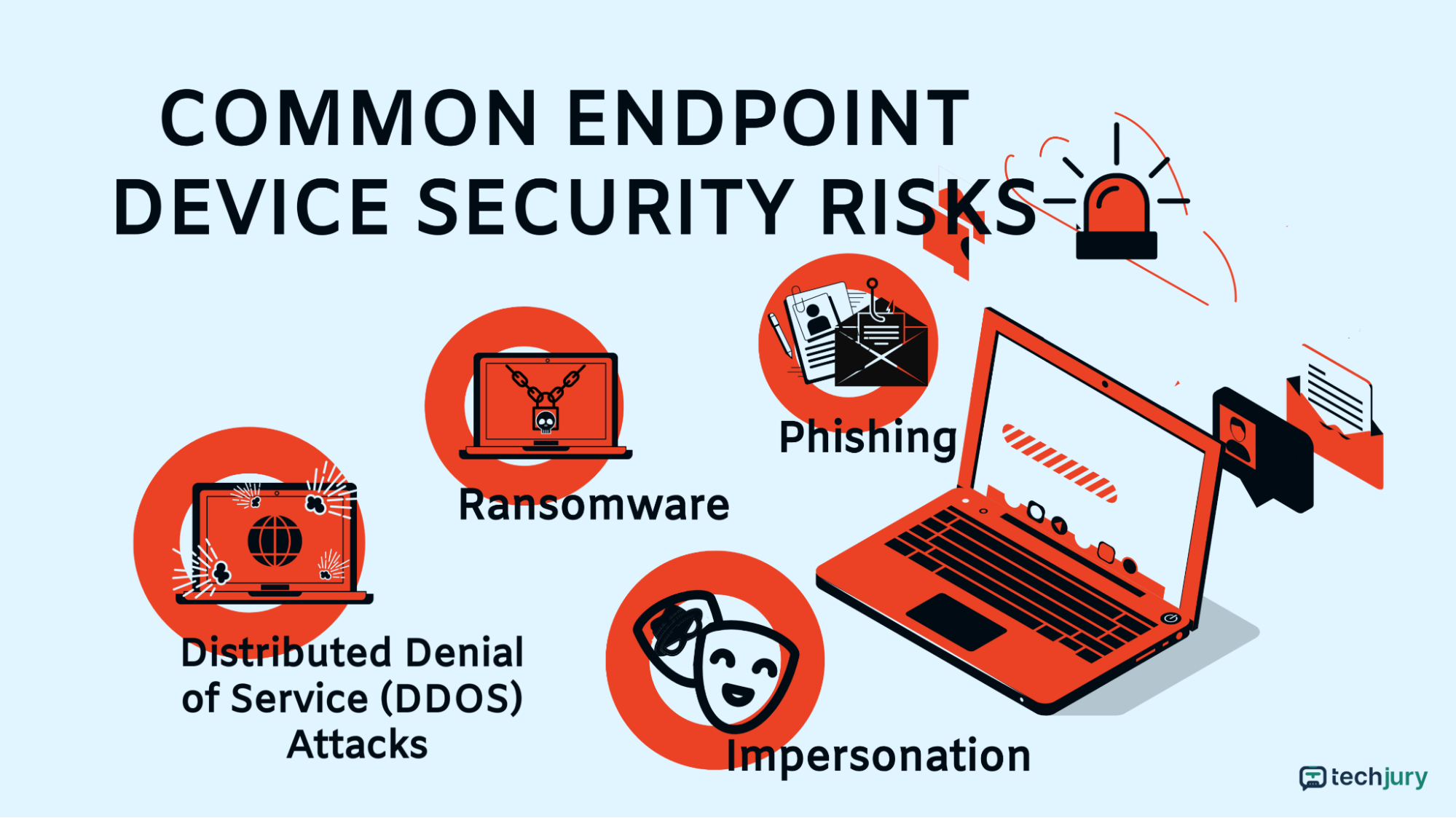
Below are the most common security risks unmonitored endpoints can bring. These “doors” can invite the following attacks:
Common Endpoint Device Security Risks
FBI’s 2021 Internet Crime Report revealed phishing as the most common cybersecurity attack. The following year, that cybercrime’s prevalence remained unchanged, with over 500 million phishing incidents reported.
An attacker deploys ransomware without the user’s knowledge and encrypts all the data in an endpoint device. Once downloaded, the ransomware holds data hostage by locking users out. It encrypts the data unless the victim pays a ransom.
|
💡 Did You Know? Ransomware has been around since 2017. According to the latest hacking trends, ransomware gets its largest payoffs from the manufacturing industry. In 2020 alone, it cashed out $2.04 million from its victims. |
Hackers use an endpoint device as part of a botnet, a group of devices infected with malicious software. The bots then enact the DDOS attack and prevent users from accessing connected websites and online services.
Hackers perform lateral movement within the network quickly. They can move through the compromised environment and get increased privileges until they reach their end goal.
|
✅ Pro Tip: Stop DDOS and other cyberattacks with Packet Capturing (PCAP). This process helps monitor network traffic and detect unusual spikes. It aids cybersecurity teams in fighting off attacks. |
After the pandemic, protecting endpoint devices from cyberattacks has become challenging, especially for companies. The increasing remote and hybrid setups have spiked the number of devices the global workforce uses. Companies are clamoring to cover all those devices to prevent breaches.
Aside from that, experts have also identified other security risks in the workplace. These are:
The low cybersecurity awareness among employees is especially glaring. The reality is that about 91.5% of cyberattacks come from human error or insider threats. Magnified by the remote working conditions, employees can become a company’s biggest weakness.
Cybersecurity specialists recommend a policy-based approach in endpoint security to deal with threats appropriately. That includes more awareness training for employees of all levels.
|
✅ Pro Tip: Endpoint Detection and Response (EDR) is the best security solution for protecting endpoint devices in a network. It’s more powerful than an antivirus because it’s proactive and gives real-time visibility to an IT infrastructure. |
As mentioned, bad habits among endpoint device users can affect the entire network’s security. There’s a higher risk if a user doesn’t know how to protect their devices.
Here are the pitfalls of endpoint devices to be aware of:
Device loss is a common cybersecurity risk. Employees who lose endpoint devices connected to the company network in a workplace setup may expose their network to attacks.
Malicious actors can use any of your systems' weaknesses, including old security suites. Poor adoption of security updates or out-of-date operating systems makes your devices vulnerable.
You have to upgrade your endpoint device’s security. Most security tools have an option for you to turn on automatic updates so that it happens without your input. Updates contain new features, bug fixes, and performance improvements to boost security.
Encryption is a security technology that protects your device from unauthorized access. It encodes information, so only authorized persons can read it. Think of it as a second layer of security for data. For example, users can use available software to encrypt their hard drives.
Endpoint device users can switch this option on or off to suit their needs. However, toggling this can lead to unwanted access points.
|
👍 Helpful Articles: One of the keys to protecting endpoint devices is acquiring knowledge. Below are articles, invaluable resources to expand your understanding of cybersecurity: |
Having an endpoint device with access to your workplace’s network and data assets is not just a privilege– it’s a responsibility, as these devices are innately vulnerable to attacks.
Remote work scenarios have employees primarily operating endpoint devices with high autonomy but little security awareness. So, aside from high-end and updated cybersecurity suites, employees must also have proper education, compliance management, and risk mitigation.
One cautious employee can make a lot of difference.
A router is a network equipment that routes traffic from one network to another. It is not an endpoint device as it is considered a CPE or customer-premise equipment hardware that is physically installed at a customer's location. Other CPEs include switches, load balancers, network gateways, and firewalls.
Devices that provide connectivity to end devices are called intermediary devices. They connect individual hosts to the network and ensure that data flows across. These include firewalls, routers, and switches/wireless access points.
A device is not considered an endpoint if it forms part of the network. These devices allow endpoint devices to talk to each other, like routers.
Endpoint devices are physical devices that serve as access points to an enterprise network. Without it, we wouldn't be able to connect to the web.
Your email address will not be published.
Updated · Feb 11, 2024
Updated · Feb 11, 2024
Updated · Feb 08, 2024
Updated · Feb 05, 2024



