

Updated · Feb 11, 2024
Updated · Nov 17, 2023
Martynas Klimas is a versatile writer, covering various fascinating topics with expertise. He has a ... | See full bio
Girlie is an accomplished writer with an interest in technology and literature. With years of experi... | See full bio
A Virtual Private Network (VPN) is an anonymity tool that lets users access the web safely.
It offers multiple servers from different countries and cities, allowing you to browse the Internet with a different IP address.
More than 1.6 billion people use VPNs, and their primary reason is privacy and safety. Encryption is what makes any VPN secure, but not everyone understands what it is.
Read on to learn more about what VPN encryption is and how it works.
|
Definition Encryption is the process of transforming a text or any piece of information into an incomprehensible format or code. Only the sender and receiver of the message can decrypt the encrypted information using an encryption key or cryptographic key. It came from the Greek word “kruptós” or “kryptos,” which means hidden or concealed. |
One of the oldest forms of encryption is ROT13. It uses the rotation of letters in the alphabet to encrypt or decrypt the text.
If you take a text and replace every letter with the letter thirteen places down, it will be unreadable to anyone who does not know what you did.
ganit
However, that method is now effortless for a modern computer.
That is why modern VPN encryption now uses more contemporary methods like AES-256 algorithms. Modern techniques usually take practically forever to decrypt.
VPN uses encryption to keep your data safe from anyone trying to intercept it between your device and the VPN server.
Here’s how it happens:
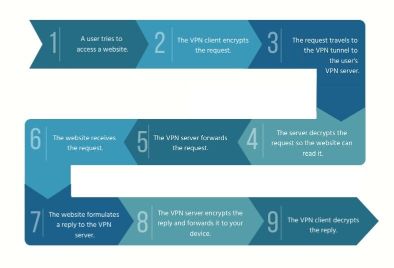
VPN Encryption Process
As soon as the VPN client decrypts the response, the user can now access the website.
The previous section is a basic explanation of how encryption in VPN works. You can better understand how everything works by taking a closer look at the four principles of VPN encryption.
Check out each one below:
Asymmetric key exchange exists to provide a way to exchange cipher keys securely over an unsecured internet connection.
This can’t be done using the normal process, which is by sending a key from the VPN client to the VPN server. It can be intercepted by parties spying on you. That is why asymmetric encryption is used.
Here’s how it works:
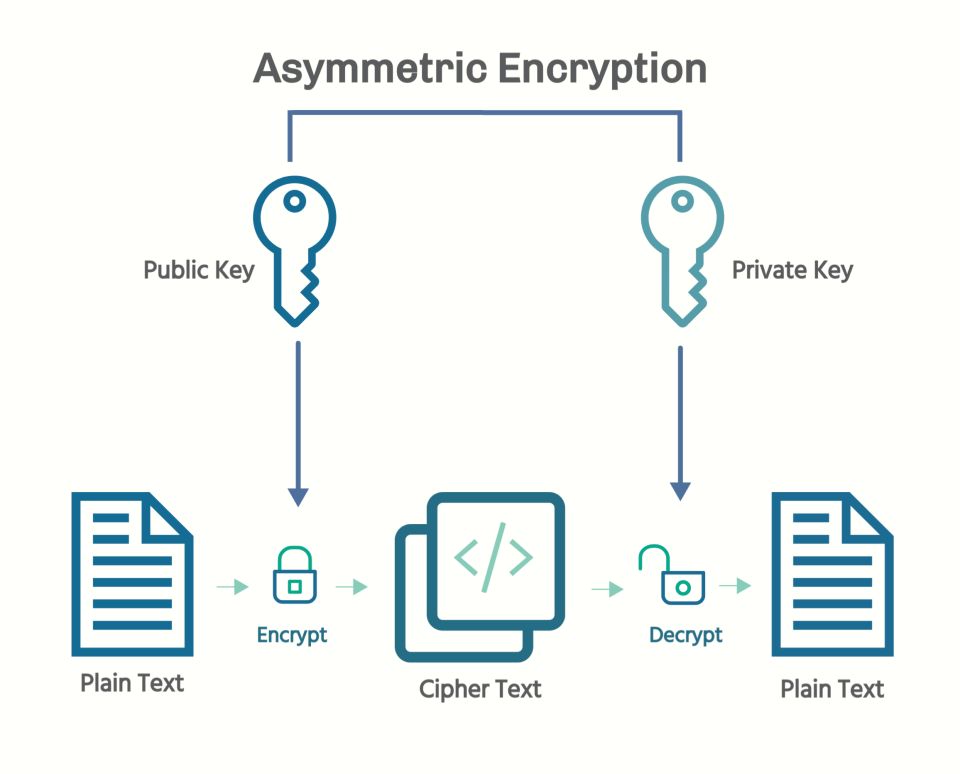
Asymmetric Encryption Process
Each session between the sender and receiver uses different keys so that even if the previous session were compromised, the new one would not be affected by it.
Having the ability to exchange keys over an unsecured medium safely is called perfect forward secrecy.
|
If you want to learn more about how encryption works, subscribe to Surfshark’s newsletter. |
Symmetric key exchange simply means that both sides of the communication use the same encryption key.
However, this is a much faster and less resource-intensive method to use than asymmetric encryption. This encryption will be used for the actual information exchange.
To get a better grasp of what it is, check out the video below:
|
Video: How Internet Encryption Works (1:25 - 2:04) |
Encryption algorithms are what take the place of ROT13 in VPN encryption. However, the ones in use today are a lot more sophisticated.
Premium VPNs like Surfshark use the AES-256-GCM version. This version breaks down your data into blocks and then applies a different encryption key to each piece.
Every block goes through 14 rounds of transformation before it’s considered to be encrypted. To successfully guess the cipher key, someone would need to make 2256 guesses.
It is impossible to do that within a human lifetime with current technology. As such, AES-256 is very secure.
GCM stands for the additional math added to the algorithm that makes it work faster than usual.
|
Fun Fact: AES-256 is incredibly secure. It would take billions of years for the most powerful computers to break it, even if everyone on Earth tried to crack it together. |
Integrity algorithm ensures the data has not been messed with during the transfer.
For that, it uses a mathematical hash function to compress an input of any length into a short output. For example, turning ABC into D.
The hash function should be hard to reverse engineer. That means you shouldn’t be able to get ABC from D.
At the same time, you must ensure that only ABC is hashed into D, with no other input.
In the end, you only need to get the hash of the message to compare it to the original hash to determine whether you got the real thing.
The real thing is even more complicated, like using the hash value of the first message block to become the input for the hash of the second message block and so on.
All these actions may seem complex, but modern hardware does it all in the blink of an eye after the user clicks the Connect button on the VPN app.
|
In a Nutshell |
A VPN protocol describes all the procedures and specific tools used to create and maintain a VPN connection.
It outlines how asymmetric and symmetric key exchanges are made, what kind of encryption is used on the data, and the types of security measures like integrity algorithms.
Currently, all good VPN protocols use a version of AES-256 encryption. Below is a table indicating what encryption each protocol uses:
|
Protocol |
Encryption |
Use |
|
WireGuard |
ChaCha20 |
The newest setup used by premium VPNs like Surfshark |
|
OpenVPN |
AES-256 |
The extremely reliable and widely-used open source stand-by |
|
IKEv2 |
AES-256 |
Good to use, especially for mobile devices |
|
SoftEther |
AES-256 |
Decent everyday use option |
|
SSTP |
AES-256 |
The Microsoft tunneling protocol for Windows devices |
|
L2TP/IPsec |
AES-256 |
Made entirely obsolete by IKEv2 |
|
PPTP |
128-bit |
If your device can support anything newer, you have no reason to use this |
Outside of obscuring your IP by routing data via the VPN server, a VPN ensures privacy from snoopers by encrypting all the information that goes through it.
Understanding the exact method for how it does it isn’t important. However, it helps you understand your tools better. Also, if you are on the lookout for a good VPN, check out Surfshark!
Yes. However, free VPNs use weaker encryptions, so they are more vulnerable to hacking.
The safest encryption is AES. It is harder to crack compared to other encryption styles. Even the US government and modern VPN services use this type for first-rate security.
People use VPNs for different reasons and benefits. However, the three primary uses of a VPN are to mask a user’s actual IP address, circumvent geo-blocking, and protect personal information.
Your email address will not be published.
Updated · Feb 11, 2024
Updated · Feb 11, 2024
Updated · Feb 08, 2024
Updated · Feb 05, 2024



