

Updated · Feb 11, 2024
Updated · Aug 26, 2023
Raj Vardhman is a tech expert and the Chief Tech Strategist at TechJury.net, where he leads the rese... | See full bio
If I was asked to describe myself using just a few words, I’d go with digital marketing expert, ex... | See full bio
A cryptographic hash function is a mathematical algorithm to validate data. Its function is to protect information's confidentiality, integrity, and authenticity.
In blockchain technology, cryptographic hash functions make the Blockchain secure. Security on the Blockchain is essential since it performs a lot of real-time data transfers.
However, like any other technology, Blockchain faces potential threats. In 2018, a hacker stole over $500 million worth of cryptocurrency. It was one of the biggest blockchain hacks on the Japanese exchange Coincheck.
Even blockchain transactions with hashing algorithms are vulnerable to hacking. Fortunately, the cryptographic hash function helps provide a strong layer of protection.
Let’s dive deeper into how the cryptographic hash function works and its other applications.
|
🔑Key Takeaways
|
In cryptography, a hash function is a deterministic procedure that takes an input and returns a fixed-sized character string called a hash digest. This output is unique compared to the input.

|
📖Definition: A hash function is any function that maps a random data size to a specified value. |
A cryptographic hash function is a hash algorithm that is used in cryptography. It is a group of specialized hash functions that provide increased security in digital transactions.
It should be noted that these are not the same as the hash functions you use in hash tables. Cryptographic hash functions have specific properties that the former doesn't.
Information security applications and cryptocurrencies are the typical uses for cryptographic hash functions.
|
Want to know more about cryptographic hash functions? Meet the computer scientist Ralph Merkle one of the inventors of public key cryptography. The computer scientist Ralph Merkle: inventor of cryptographic hash functions, one of the inventors of public key cryptography, and the creator of Merkle Trees (which are essential to the efficiency and integrity of blockchains) 🌲 |
Information is passed through a Hashing Algorithm Function as it becomes the input.
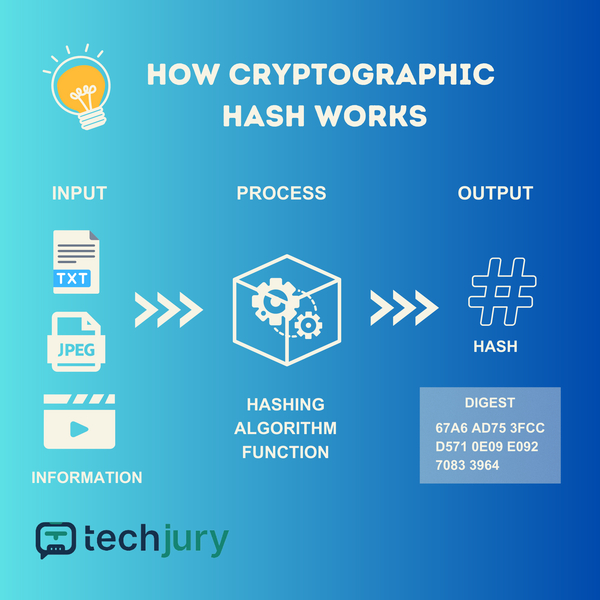
A mathematical operation now processes the input. These are the Hashing Algorithm functions, wherein there are different types of Hashing Algorithms. Then, what gets out is a string of fixed lengths of data. This string is what we call a digest or hash. The hash is composed of numbers and letters.
Cryptographic hashing works by processing information with hashing algorithms, which results in a hash.
Having discussed how information is passed through the functions of hashing algorithms, take a look at the ideal properties of the output of a cryptographic hash function.
When creating cryptographic hash functions for cryptographic applications, certain properties are desired, such as:
1. Deterministic
Regardless of the input, it will always have the same output hash. For example, when hashing one sentence, the output should be the same as when hashing an entire book.
This property is essential for verifying the integrity of the information received.
2. Fast Hashing
It should be fast since it relies on bitwise operations, which are easy to compute. Hashing algorithms must operate at a fast pace.
Quick computation of output hash values is an ideal property of a cryptographic hash function.
3. Irreversible
They are irreversible. Identifying the input information using the hash function's output is difficult. This property is also known as one-wayness.
4. Collision Resistance
It should be collision resistant. Two different messages can't produce the same hash output.
The goal of collision-resistant is to make the probability of two inputs sharing one output negligible.
5. Uniformity
If the input message changes slightly, the output significantly changes from the old one. There is no correlation between the old and new hash codes.
An alteration to the message creates a hash. Then the same hashing algorithm should significantly change the hash value. This property is commonly known as the avalanche effect.
The properties of a cryptographic function are essential to determining a good hash function. While the hashing algorithm is vital for the hash function, different hashing algorithms are used when sending files.
An essential element in the cryptographic hash function is the hashing algorithm. A hashing algorithm is a method of sending essential files.
Here are different types of hashing algorithms:
MD–5, which stands for Message Digest, is the first hash algorithm available since 1992. Besides being the most common hash algorithm, it is also the least secure.
It converts the data into a string of 32 characters. Primarily, it is used to authenticate files.
SHA-1 means Secure Hash Algorithm 1. It is a one-way cryptographic function that can convert any message to 160 bits.
In previous years, it has been used for digital signatures, file integrity checks, and cryptographic applications. However, there are vulnerabilities in SHA-1. Nowadays, it is considered insecure.

SHA - 256 is one of the successors of the hash function SHA - 1. It is also one of the strongest hash functions.
SHA-256 is a virtually irreversible hash used to verify the data's authenticity. Additionally, it is one of the most widely used hash algorithms.
SHA-512 is used for a cryptographic hash function. It can produce a 512-bit hash. It was introduced in 2001.
It is commonly used for applications that require a high level of security.
Bcrypt is a password hashing function. It was designed by Niels Provos and David Mazières in 1999. At the same time, Colin Percival first presented the scyrpt in 2009.
Both Key derivation functions of the two ashing Algorithms are designed to be slow on a computer. However, Scrypt is the most secure compared to Bcrypt.
Bcryot is used for simple passwords, while Scrypt Scrypt is used in many cryptocurrencies as a proof-of-work algorithm.
The wide use of cryptographic hash functions proves its versatility—there are many practical applications where cryptographic hashes are important to ensure the security and integrity of their processes.
Cryptographic Hash functions are used in many ways. Listed below are the various uses of cryptographic hashes:
Cryptocurrency
The most common use for cryptographic hashes is in cryptocurrencies. It is used to pass anonymous transaction information.
It is also used for generating public jets and block hashing. Take Bitcoin as an example. The hash function used for its algorithm is SHA - 256.
|
👍Helpful Article: If you’re new to the crypto world, a beginner-friendly cryptocurrency article might be best for you. It is also worthwhile to learn about current cryptocurrency statistics, or simply know how many cryptocurrencies are out in the market. |
Verification of Password
Websites use hashes to store passwords because text files are dangerous. Text files are easily copied and prone to data breaches.
Unlike hashes, it does not reveal the origin password whenever hackers retrieve the password. Moreover, password hashes can be compared quickly and easily, making verification faster.
Digital Signature Generation and Verification
A digital signature is a method by which a person's entity is linked to digital data. It utilizes mathematical data to verify the authenticity of a digital message or document.
Cryptographic protocols use digital signatures as a standard element for software distribution, financial transactions, and other cases where it is critical to detect forgery or tampering.
|
✅Pro-tip: Look at the Techjury reviews of the best digital signature software on the market to make an informed decision based on security needs. |
File Authenticity Verification
File verification uses an algorithm to detect tampered files. The most common way to verify a file's authenticity is to generate a copy of its hash. The generated copy is then compared to the hash of the original file.
However, using the classical hash function is insufficient because it is not designed to be collision resistant. This is why cryptographic hash functions are often used for file authenticity verification.
As long as the hash sums cannot be tampered with, files can be presumed intact.
Blockchain
In blockchain technology, a cryptographic hash function is used to secure connections and message transmission between blocks in a chain.
Each block contains a hash of its own and the previous block's hash, which forms a cryptographically secured chain of blocks.
A cryptographic hash function is a significant part of maintaining information security. It is used to protect information's confidentiality, integrity, and authenticity.
However, only some people know about the cryptographic hash function. Many think that it is complicated and hard to understand.
Fortunately, we break down all the essential information about cryptographic hashes and how they work.
A cryptographic hashing algorithm takes a variable-length input and generates a 256-bit hash.
It is a fixed-size numeric value that can uniquely identify data.
Yes, hashing can add security; however, passwords should only be hashed in certain circumstances.
Your email address will not be published.
Updated · Feb 11, 2024
Updated · Feb 11, 2024
Updated · Feb 08, 2024
Updated · Feb 05, 2024



