

Updated · Feb 11, 2024
Updated · Nov 16, 2023
Aditya is an Azure DevOps and Infrastructure Virtualization Architect with experience in automation,... | See full bio
Lorie is an English Language and Literature graduate passionate about writing, research, and learnin... | See full bio
Secure Socket Shell (SSH) is a network protocol that allows two machines to communicate and share data. It encrypts data transferred so information is not in plain text.
After 25 years since its inception, 95% of internet-powering servers use SSH. Until now, organizations still seek the security that SSH offers.
You can find out why in this article. Read on to learn more about the basics of SSH, how it works, and its benefits.
|
🔑 Key Takeaways
|
As a network protocol, SSH allows administrators to securely “log in” to remote assets without physically accessing the device.
Through SSH, administrators can perform basic operations such as file transfers, deliver software patches, and manage systems remotely.
SSH encrypts the connection between endpoints, making it an effective alternative to legacy login protocols and insecure file transfer methods.
There are two main SSH versions: SSH-1 and SSH-2. Find out the key features of each version in the table below.
|
SSH-1 |
SSH-2 |
|---|---|
|
Provides a strong host-to-host and user authentication |
Has twice the security power and covers the vulnerabilities of SSH-1 |
|
Allows encrypted communication using the following algorithms:
|
Supports the following encryption algorithms:
|
|
N/A |
Supports the secure version of FTP |
|
Single monolithic protocol with no ability to customize transport, authentication, and connections |
Utilizes a modular approach with independent transport, authentication, and connection protocols |
|
Has weak CRC-32 integrity check |
Uses a strong cryptographic Message Authentication Code (MAC) |
|
N/A |
Supports the changing of passwords |
|
Has one session channel for each connection |
Can run multiple shell session channels |
|
Has more fixed parameters and negotiates only the bulk cipher |
Full negotiation of cryptographic and compression algorithms |
|
Employs the same algorithms and keys for incoming and outgoing connections |
Encryption, MAC, and compression are negotiated independently for each connection’s direction |
|
Has fixed encoding and might not cater to new features and updates |
Extensible algorithm that allows local extensions while still preserving interoperability |
|
Supports:
|
User authentication methods:
|
|
N/A |
Allows public-key certificates for authentication purposes. |
|
A single authentication form is enabled per session. |
User authentication exchange is flexible |
|
Rhosts RSA authentication is tied to the client host address. |
Authentication is independent of a client network address |
|
N/A |
Periodic change of session keys |
SSH-2 provides enhanced security and functionality compared to SSH-1.
The former addresses the vulnerabilities of the older version with its robust encryption (i.e., AES and Blowfish) and improved authentication.
The modular design of SSH-2 allows independent customization, while its cryptographic processes assure adaptable and secure data exchange.
SSH uses symmetric encryption, asymmetric encryption, and hashing to secure data transmission.
The SSH connection between server and client can be documented in three stages: verification by the client, generation of a session key, and client authentication.
Here’s how each process works:
The client tries to initiate an SSH connection with the server. If the client connects to the server for the first time, he needs to authenticate the server manually.
This is done by verifying the public key of the server. Once the key is confirmed, the server gets added to the known_hosts file in the ~/.ssh directory.
The server’s identity will automatically match what was previously recorded in the known_hosts file. This is if it’s not the first time the client has initiated an SSH connection.
If the server identity is successfully verified, it’s time to generate a session key.
Both parties will now negotiate a session key using the Diffie-Hellman algorithm. This algorithm allows both parties to contribute equally to generating a session key.
|
🎉 Fun Fact The Diffie-Hellman algorithm is a cornerstone of modern cryptography. It was invented by Whitfield Diffie and Martin Hellman in 1976. This method lets two parties securely exchange cryptographic keys over an unsecured channel. Its security relies on the difficulty of solving the discrete logarithm problem. |
Authentication is done using the SSH key pair. The SSH key pair is a pair of two keys with different purposes.
The first key pair is a public key freely shared and is used to encrypt data. The second pair is a private key used to decrypt data.
After the symmetric encryption happens, the flow of authentication of the client goes as follows:
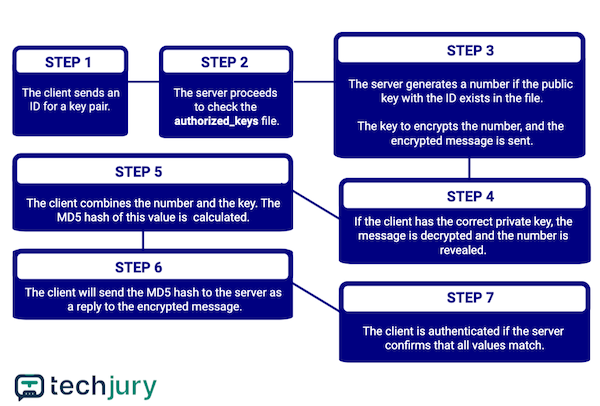
By using SSH, you have more control than what a standard web-based graphical interface allows.
Find out what other specific benefits SSH has for your organization:
Allows automated file transfers
SSH allows users to transfer files securely. It also supports tools that automate file transfers, such as Secure Copy and Secure File Transfer Protocol.
Enables remote commands
SSH lets you log in remotely and run commands on a machine as if you’re physically typing directives. This feature is helpful when managing multiple servers at once.
Lessens the failure rate of IP source routing
IP source routing allows the sender to define which route the packet needs to go and where to return. Sometimes, this fails if malicious users intrude.
SSH lessens the fail rate of source routing by encrypting the connection over a network. Also, it adds another layer of protection by authenticating the computer.
Prevents IP Spoofing
IP spoofing is modifying a source address to hide or impersonate a computer. It invokes malicious attempts to disrupt the target device or its surrounding infrastructure.
SSH’s capability to encrypt tunnels and authenticate users makes it difficult for attackers to try to modify data in transit.
Blocks DNS Spoofing
DNS spoofing is a cyberattack in which users obtain sensitive information through an altered domain name, redirecting traffic to another site.
SSH’s extra security in the communication channel between two computers prevents malicious users from intercepting the data.
Wards off eavesdropping on transmitted data
Without SSH, you’re using an unsecured connection—and attackers can watch every data that goes through. They can collect data to your disadvantage.
|
⏳ In a Nutshell SSH provides organizations with control beyond web interfaces—enabling secure file transfers and remote command execution. It also provides robust security against several IP issues. SSH features collectively bolster network security, data integrity, and operational efficiency. |
See how SSH evolved from a mere response to a password-sniffing attack to an unavoidable protocol system for network administrators.

After the latest password-sniffing attack at Finland’s Helsinki University of Technology in 1995, Tatu whipped up a cryptographic network protocol. He called it SSH1.
Beta versions of the protocol started popping. Tatu’s SSH team realized that the protocol needed to be free to reach a wider audience of system administrators.
|
🎉 Fun Fact In July 1995, SSH1 was offered as free software. The decision to allow the public to copy SSH1 amassed 20,000 users in 50 countries by the end of that year. |
SSH continues to be free with liberal licensing. By December 1995, Tatu began commercializing SSH and founded the SSH Communications Security Corporation (SCS).
As SSH-1 grew in popularity, it was inevitable for its limitations to get noticed.
Since it’s impossible to fix the problems without losing backward compatibility, SSH-2 was born. SSH-2 or SSH 2.0 includes new algorithms that address what SSH-1 cannot.
Due to the growing public interest, the Internet Engineering Task Force attempted to regulate SSH-2 by forming the Secure Shell.
The SSH-2 software was based on the superior SSH-2 protocol. However, the software didn’t replace SSH-1 entirely. It was missing some of the key SSH-1 features.
The OpenBSD Project introduced a free implementation of the SSH-2 protocol called OpenSSH.
Although several sources contributed to the creation of OpenSSH, Markus Friedl is largely credited for his contribution to the project.
It was ported successfully to several operating systems like Linux, Solaris, AIX, MacOS X, etc.
SCS continued to improve SSH and its products. Now, its product line carries the name Tectia. Currently, SSH implementations also have free and commercial versions.
In 2017, SSH even secured port 22. According to the SSH creator himself:
|
SSH made itself an indelible part of the IT industry and the Internet. Through it, encrypting communications between SSH client and server is simplified.
Despite being developed in the 1990s, SSH is still considered the superior protocol over other authentication methods.
Any business that requires security with file sharing and internet communication needs SSH in its IT toolbox.
Yes. PuTTY is an SSH client. It’s a free terminal emulator that acts as a client for SSH and other protocols.
To use SSH as a VPN alternative, you must establish an SSH connection to the server. Then, configure port forwarding rules.
SSH keys are authentication methods to gain access to encrypted connections between systems.
An SSH tunnel is a network connection that allows the transit of encrypted data over the internet.
An SSH client is a program that establishes secure and authenticated SSH connections to SSH servers.
Your email address will not be published.
Updated · Feb 11, 2024
Updated · Feb 11, 2024
Updated · Feb 08, 2024
Updated · Feb 05, 2024



